Why Cyber Security is important?
Businesses who succeed in a hypercompetitive landscape know that they must focus on innovation, R&D and use their capital budgets to increase their agility and increase their competitiveness. To gain this competitive edge on its competition, modem businesses are increasingly seeking new ways to drive innovation and growth through the extension of their data and information assets outside of traditional physical boundaries. This is the core cybersecurity challenge facing businesses today. Potential hackers and business adversaries have also recognized that these trends present an opportunity to obtain high value proprietary information for themselves with only a small expenditure of resources and risk.
Cybersecurity practices must strive to balance the focus of R&D and innovation extension of information assets to drive growth yet maintain acceptable levels of business costs and information risk. How your organization handles and protects its most valuable information assets is key to maintaining a good business reputation, meeting privacy expectation of regulators, customers, employees, and partners, as well as enabling your business to thrive in the modern, interconnected global economy.
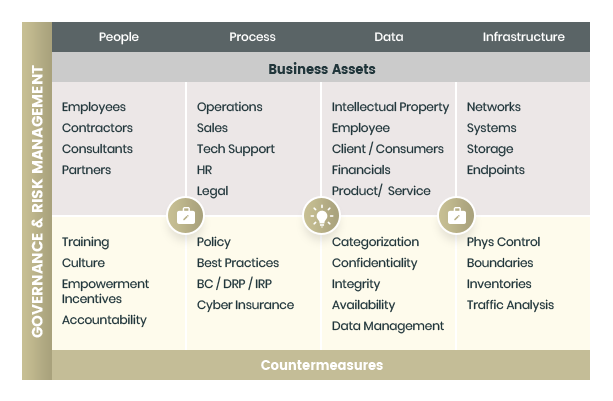
Cyber Security Solutions
- Cloud migration
- Boundary Protection
- Secure Baseline Configuration
- Assets Management
- Admin Privilege Management
- Dual Factor Authentication
Cloud migration
Why worry about keeping up with latest operating system, or applying required security patches or having newer and better version of Word, Excel, PowerPoint, and Outlook?
NSG can seamlessly move you to Microsoft 365 cloud. Once moved, you will never to worry about managing software license, patching your operating system or Microsoft applications. All your emails will be migrated and available next time you login, you will not miss a heartbeat as your events, tasks, calendar will be available at your fingertip no matter whether you are in the office working on your desktop, or your home on your phone or tablet device. We make it completely pain free for you by using experienced cloud engineer and using proven tools and processes!
Call or email us today to implement very cost-effective Cloud Migration path for your organization!.
Boundary Protection
Our print media is flooded with news about Ransomware, data, financial information stolen from Marriott, Target, OPM and other big companies and government.
To reduce these type of attacks, NSG can help you with Defense-in-Depth and Defense-in-Breadth solutions. Our experienced Security Engineers can provide comprehensive awareness of how you can improve your security. One of the most important solution is to deploy a Next Generation Firewall solution and configure with access rules.
Combining with the power of the new generation firewall and using Intrusion detection, GeoIP blocking as well as adding realtime threat monitoring and protection to enhance the protection of your network.
Call or email us today to implement very cost-effective yet a powerful Firewall/IDS solution!
Secure Baseline Configuration
Research shows that most of the attacks seen is US is because of old unpatched hardened servers.
NSG has years of experience with the federal government customers in hardening the operating system from configuration point of view. NSG have used CIS-CAT secure configuration as well as DISA's secure configuration guidelines by using Windows policy editor and other tools for Linux operating systems.
Call or email us today to implement very cost-effective approach to securing your server infrastructure!
Assets Management
Having complete control of your organization's assets is the most important and a very first step you should take to your cybersecurity needs.
NSG can help you in identifying your intellectual properties, hardware, software, applications, data flows, network boundary, external interfaces, your workforce to include employees, customers, vendors, and contractors.
Please contact us today to start getting control of your network connected assets to implement most important security control.
Admin Privilege Management
Organizations often keep their network vulnerable to the adversaries by not controlling administrator user account.
NSG's Security auditors can provide strategies to implement processes and techniques to manage privilege account use.
Dual Factor Authentication
NSG has implemented smart card login at various federal government agencies. We can assist you in deploying PKI infrastructure, technology selection, implement physical facility access using same card used to login to workstation.
Contact us today to deploy Smart card infrastructure for your facility and for logical access to the network.